Pressbooks is an open-source book content management system that exports in multiple formats: ebooks, webbooks, print-ready PDF, and various XML flavours. The system is built on top of WordPress Multisite.


Pressbooks is an open-source book content management system that exports in multiple formats: ebooks, webbooks, print-ready PDF, and various XML flavours. The system is built on top of WordPress Multisite.
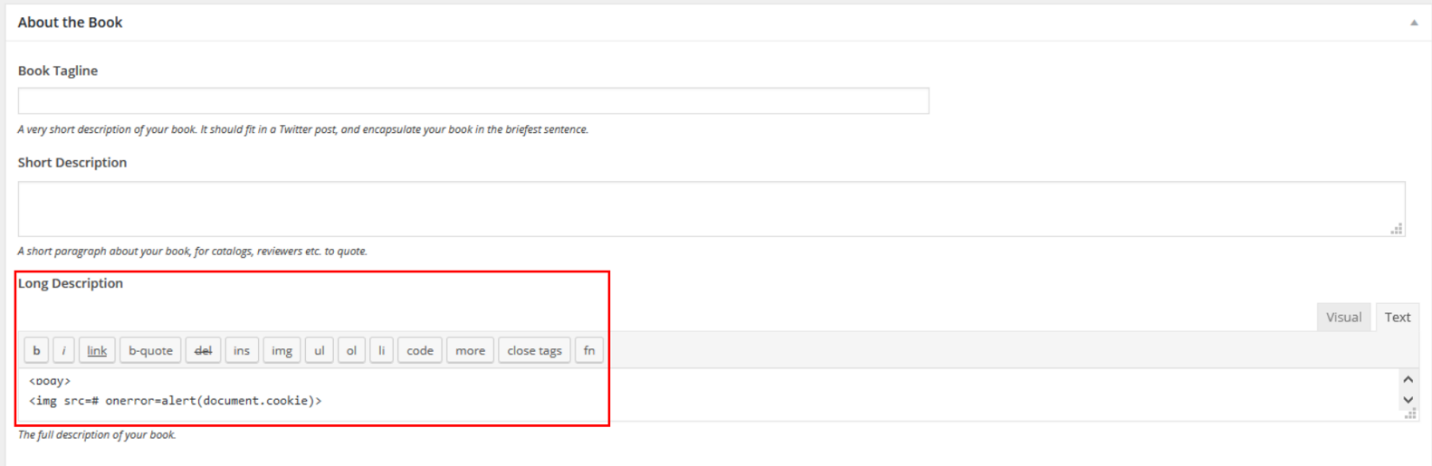
The steps to reproduce this XSS are to go to the “book info” page and then under the “long description” insert the following code:
<html>
<body>
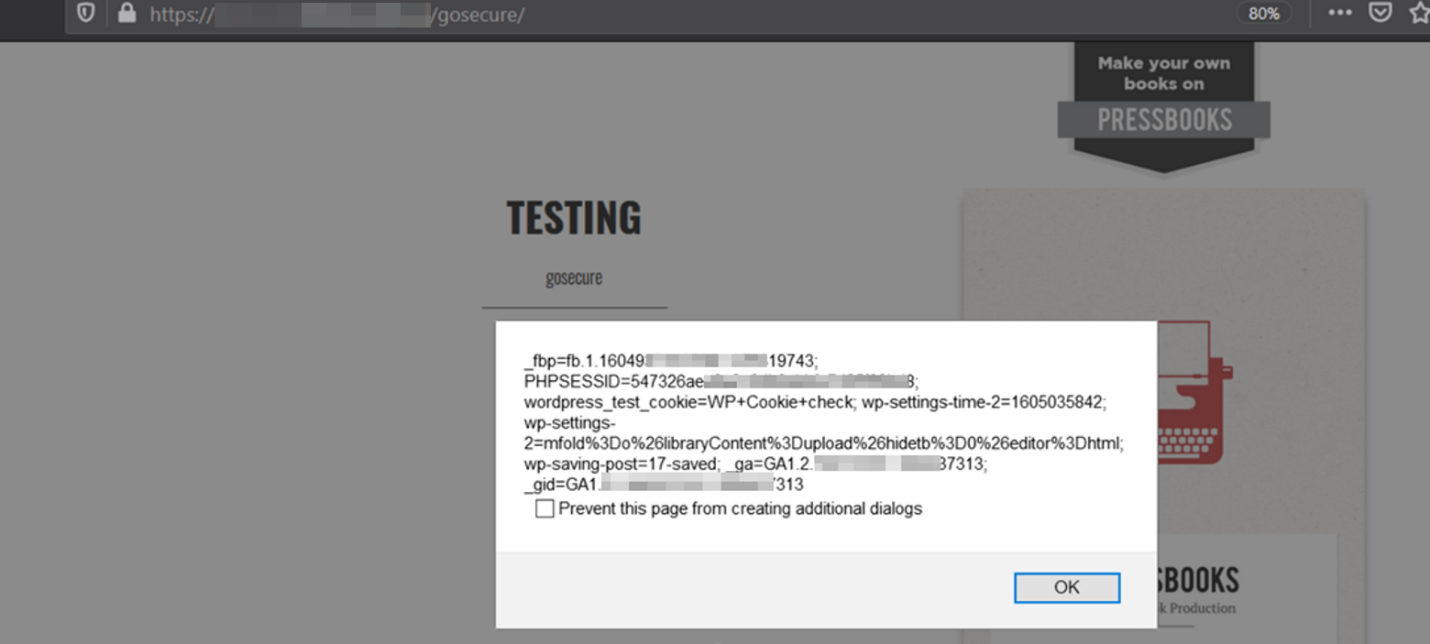
<img src=# onerror=alert(document.cookie)>
</body>
</html>Impact
A valid attack scenario would be to clone the applications login page, store it within the malicious HTML file. Once opened it would alert the end user that their session has expired promoting them to enter their credentials. This could lead to account takeover.
Technical Analysis
Vendor Response
The Pressbooks development team sanitizes metadata book info metaboxes to prevent XSS attacks on fields that allows HTML input, this uses Htmlawed to filter and sanitize the input values. The security flaw in the pressbooks application was resolved with a pull-request merged into the dev branch of the main Pressbooks repository which addresses this vulnerability. A stable version of Pressbooks was released in late January of 2021 which includes this fix.
Timeline
- Disclosed to the vendor January 1st, 2021
- Acknowledged and fix was published to the dev branch on January 13th, 2021
- Retests confirmed fix of vulnerability January 13th, 2021
- CVE assigned January 22nd, 2021
Conclusion
Unsanitized user-input continues to be a concern in Web applications even after years of developer awareness. Although a textbook XSS, we believe publishing proof of concept for vulnerabilities like this is important as an incentive for organizations to patch.
Assigned CVE-2021-3271
Clients of GoSecure Managed Detection and Response (MDR) with the Network Detection and Response component have detection capabilities in-place in case of exploitation of this vulnerability.